DATA CENTER
At CYBERPOMP, your data accumulated through online interactions is your Living Digital Identity's biggest asset. Here, we show you how your data is managed and utilised to cultivate your Living Digital Identity.
1. What does the Living Digital Identity achieve?


First, CYBERPOMP asks what you hope to achieve with your Living Digital Identity. For instance, Yolande, our Entruster, may be an introverted person. She wishes that her Living Digital Identity portrays the more fun-loving and candid side of herself, which she sometimes finds more difficult to show in face-to-face interactions.
2. Multi-faceted Communication
Second, Yolande lists down all online communication channels that she has used, or has been using.
With Yolande’s permission, CYBERPOMP scans through her data on these accounts and picks up information integral to Yolande’s personality, hobbies and interests. This may include status updates, photos, videos, and even voice messages.
Each online platform may portray a different side of her, depending on who she is connecting with. As such it is important to determine as many facets of an Entruster before moving on to the next step.
3. Mix & Match
Third, Yolande chooses which aspect(s) of these facets align the most with what she wants to achieve as a Living Digital Identity. She can also control the degree of how much of her Living Digital Identity draws from this facet.
CYBERPOMP feeds the data specified in Yolande’s preferences through our state-of-the-art artificially intelligent neural network, which readies itself for activation when she passes away.
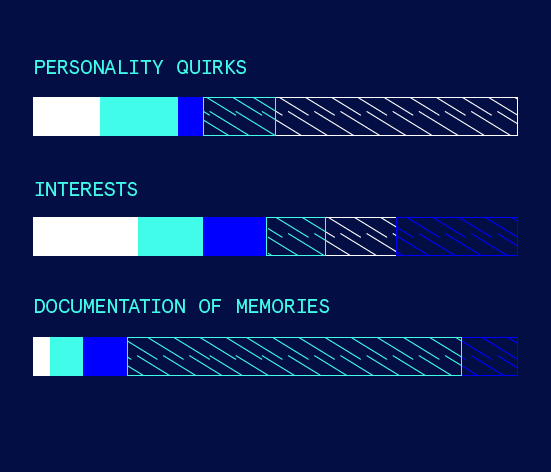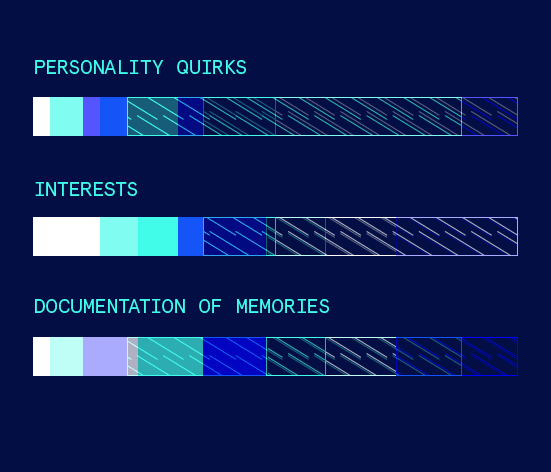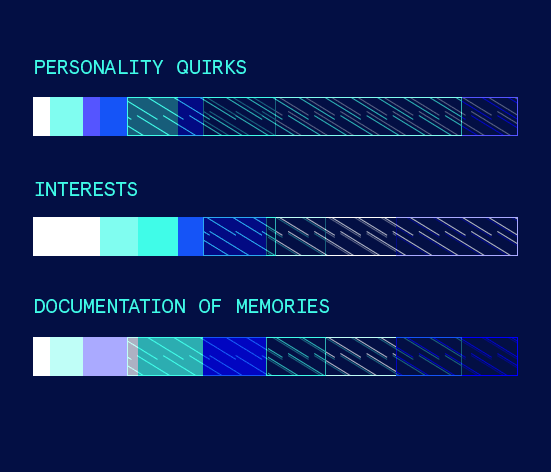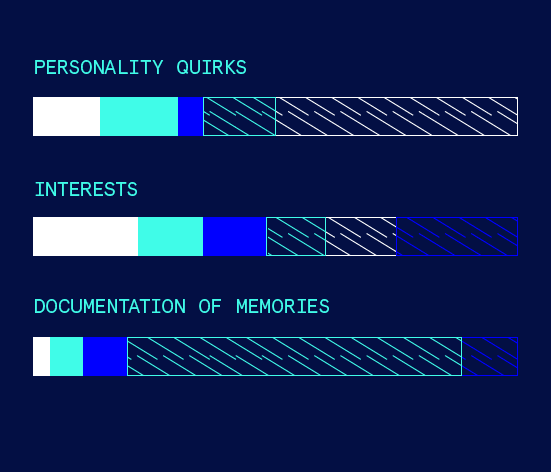


These preferences are locked down with Yolande’s acknowledgement. At any time, Yolande can edit these preferences whenever she changes her mind.
When activated, Yolande's Living Digital Identity draws from data that she has customised, and is an autonomous entity that communicates with her loved ones and friends, or just about anyone who chooses to reach out to her.
Just like old times.
